Uber hack - two lessons
- Sep 21, 2022
- 1 min read
The recent Uber breach is already a well established pattern: it appears the perpetrator is the same gang responsible for attacks against Microsoft, Cisco, Samsung, Nvidia and Okta, among others.
Many will recognize the attackers are always starting with trivial social engineering tactics: tricking an employee to allow access to an internal system. Phishing techniques are behind most today's attacks, and that's why constant and ongoing security awareness trainings (SAT) should be a norm. "Manually" driven SAT initiatives are ineffective and short lived: the effort must continuously be updated for existing employees (to cover emerging phishing techniques), and not only include new joiners. Not investing into SAT software seems to be the biggest mistake organizations make.
The other implication is the fragility of automation once phishing is successful. See how the Uber hack progressed:
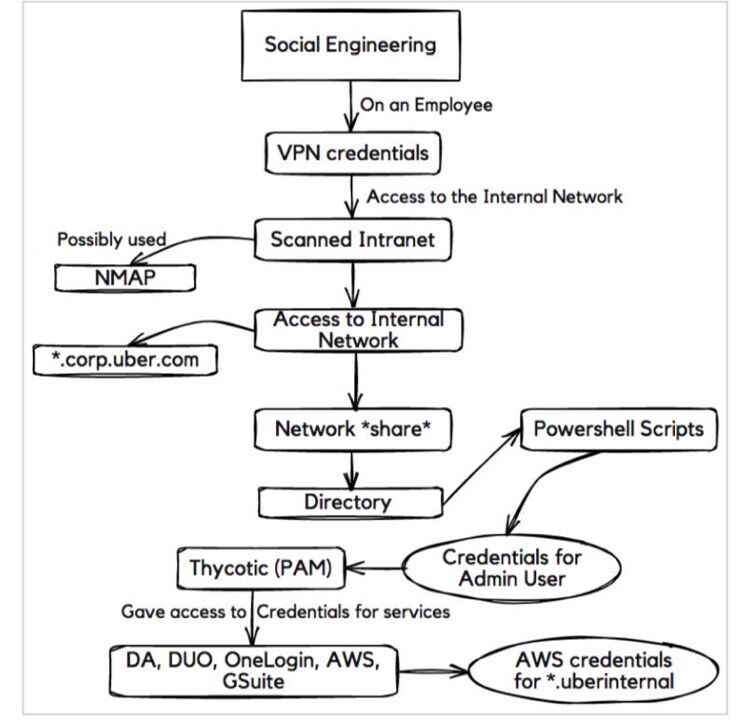
The key step above was the discovery of highly privileged access credentials in a Powershell script, which allowed the attacker to access application and infrastructure services across the organization.
Companies are increasingly relying on automated tasks via scripts and API calls to run IT operations. IT infrastructure is converging to a model called infrastructure-as-code, where provisioning of network and compute resources can be orchestrated via software.
Although the productivity gains are clear, automation often implies saving credentials as clear text into scripts or other locations. These can then be discovered and used by malicious actors who have a foothold on the system. To make things worse, the credentials used by automated tasks are often the ones with the highest privileges.
The lesson: besides investing in phishing protection and SAT trainings, admins should take saved credentials as "radioactive" material - apparently laying inert, but capable of great damage.

![[Webinar] NIS2 is Here - What Now?](https://static.wixstatic.com/media/6681e7_beb47411e54f424c8b934c85bd5b487b~mv2.png/v1/fill/w_250,h_250,fp_0.50_0.50,q_35,blur_30,enc_avif,quality_auto/6681e7_beb47411e54f424c8b934c85bd5b487b~mv2.webp)
![[Webinar] NIS2 is Here - What Now?](https://static.wixstatic.com/media/6681e7_beb47411e54f424c8b934c85bd5b487b~mv2.png/v1/fill/w_305,h_305,fp_0.50_0.50,q_95,enc_avif,quality_auto/6681e7_beb47411e54f424c8b934c85bd5b487b~mv2.webp)



