Snowflake Attack and the Urgency of MFA
- Admin
- Jun 16, 2024
- 3 min read

Any internet-facing asset requiring authorization should be secured by multifactor authentication (MFA). That is especially true for cloud and SaaS providers, as Snowflake recently discovered.
Snowflake is a multi-cloud data warehousing platform used to store and analyze large amounts of structured and unstructured data. Many customers worldwide rely on Snowflake for various data analytics tasks, with industries ranging from manufacturing, healthcare, and finance, to the public sector.
Crucially, Snowflake is delivered in the cloud, mainly as a software-as-a-service offering, which makes it easy for customers to onboard and start working on projects. It also means the platform hosts lots of sensitive data for thousands of companies, making it an attractive target for threat actors.
It recently surfaced that starting sometime in April 2024, database records originating from victims' Snowflake instances started appearing on the public internet. As documented by Mandiant, it turned out a threat actor was systematically compromising Snowflake customer instances using stolen customer credentials, advertising victim data for sale on cybercrime forums, and attempting to extort many of the victims.
As of today, Snowflake has identified approximately 165 exposed organizations (mostly large enterprises), which means the potential size of records exfiltrated makes it one of the biggest data breaches in recent history. Worth noting is that the threat actor campaign is still ongoing.
The lessons learned
It appears this incident is not related to any breach of the Snowflake platform. It was not caused by a vulnerability or misconfiguration of the platform, nor was it caused by compromised credentials of current or former Snowflake personnel (such as the Okta breach).
Instead, this appears to be a targeted campaign directed at users with single-factor authentication - namely, password-only protected accounts.
The threat actor has been using infostealer malware deployed on employee devices (i.e. laptops) at various Snowflake customer organizations. Such malware is usually delivered via drive-by download links, facilitated by phishing emails. Based on the number of affected customers, the malware was probably targeting passwords and access tokens from popular SaaS applications such as Snowflake.
Once they got hold of these stolen credentials, the threat actor was free to access the customer’s Snowflake instance and ultimately exfiltrate valuable data.
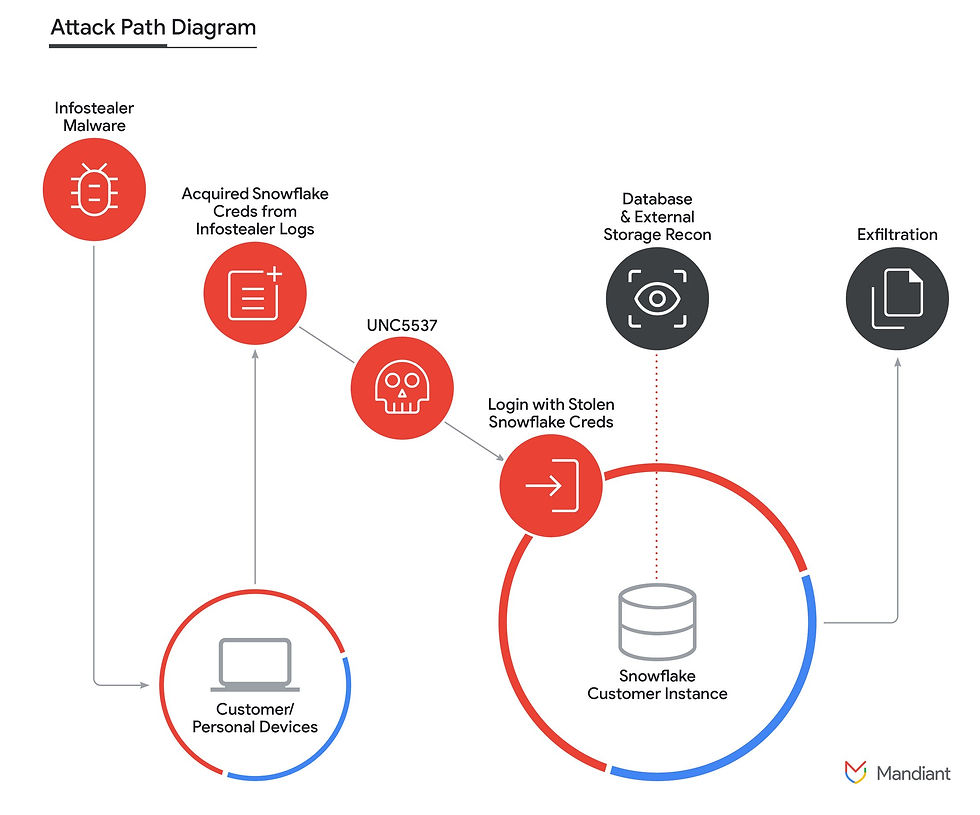
It is now clear Snowflake made the mistake not enforcing MFA usage across its customer base. They are now developing a plan to require customers to implement advanced security controls, including MFA or network policies, but in this case, it's too late.
The incident illustrates that public internet-facing assets (and especially a SaaS services) requiring any authorized access, must in fact be secured by MFA, ideally the phishing resistant type.
This is something cloud providers such as Microsoft, Google, and Amazon have found early on. They noticed their infrastructure and services were becoming infested by bots and activity related to customers' stolen passwords. Realizing the identity is a key component of the attack surface, and to prevent service degradation (supposedly not out of altruism), they started offering customers the ability to easily switch on MFA.
Microsoft started this process back in 2019, followed by Google Cloud and Amazon AWS. Nowadays, MFA is becoming an option enabled by default. Recent techniques to bypass MFA have even prompted providers to upgrade smartphone-based MFA with so-called number matching (see here).
It's therefore surprising that Snowflake has not learned this lesson in time, and is now belatedly catching up.
As a rule, when accessing any kind of protected internet-facing resource - from a self-hosted VPN to a SaaS web application, one should not rely on passwords anymore. Instead, enable MFA and prefer providers making it a setting enabled by default. Avoid those not offering MFA or charging additional fees to enable single-sign-on integrations with your MFA-enabled identity provider.

![[Webinar] NIS2 is Here - What Now?](https://static.wixstatic.com/media/6681e7_beb47411e54f424c8b934c85bd5b487b~mv2.png/v1/fill/w_250,h_250,fp_0.50_0.50,q_35,blur_30,enc_avif,quality_auto/6681e7_beb47411e54f424c8b934c85bd5b487b~mv2.webp)
![[Webinar] NIS2 is Here - What Now?](https://static.wixstatic.com/media/6681e7_beb47411e54f424c8b934c85bd5b487b~mv2.png/v1/fill/w_305,h_305,fp_0.50_0.50,q_95,enc_avif,quality_auto/6681e7_beb47411e54f424c8b934c85bd5b487b~mv2.webp)



